Pairing-Free Public Key Searchable Encryption Scheme Resilient to Frequency Analysis for IoT
DOI:
https://doi.org/10.64509/jicn.12.38Keywords:
Data security, Internet of Things, searchable public key encryption, frequency analysisAbstract
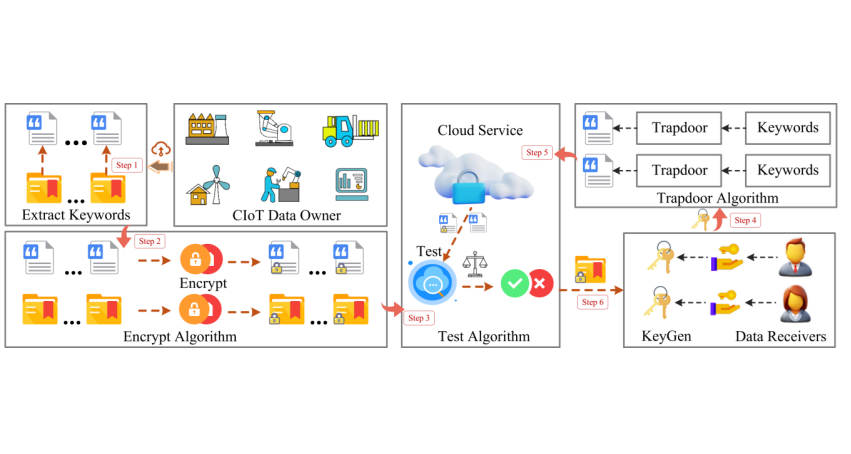
To enhance the searchability of encrypted cloud data while preserving user privacy, public-key encryption with keyword search (PEKS) has been regarded as a promising approach. However, existing schemes still incur substantial computational overhead in resource-constrained IoT environments. Moreover, IoT applications frequently reuse certain keywords during operations such as data labeling and status reporting, making them more susceptible to frequency-analysis attacks. To address this, this paper analyzes the limitations of existing pairing-free public-key authenticated encryption with keyword search (PAEKS) schemes in resisting frequency analysis and proposes a pairing-free PAEKS construction based on elliptic-curve scalar multiplication. A probabilistic trapdoor is further introduced to weaken the linkability between keywords and their occurrence frequencies. The proposed scheme effectively mitigates frequency-analysis attacks and, by eliminating costly bilinear pairings, significantly reduces computational burden. Experimental results show that, compared with conventional schemes, the proposed approach achieves lower runtime in ciphertext and trapdoor generation while providing stronger protection against frequency analysis, thereby attaining a more favorable security–efficiency trade-off suitable for IoT deployments with constrained computation and bandwidth.
Downloads
References
[1] Andola, N., Gahlot, R., Yadav, V.K., Venkatesan, S., Verma, S.: Searchable encryption on the cloud: a survey. The Journal of Supercomputing 78(7), 9952–9984 (2022) https://doi.org/10.1007/s11227-022-04309-6 DOI: https://doi.org/10.1007/s11227-022-04309-6
[2] Song, D.X., Wagner, D., Perrig, A.: Practical techniques for searches on encrypted data. In Proceeding 2000 IEEE Symposium on Security and Privacy, pp. 44–55 (2000). https://doi.org/10.1109/SECPRI.2000.848445 DOI: https://doi.org/10.1109/SECPRI.2000.848445
[3] Li, J., Huang, Y., Wei, Y., Lv, S., Liu, Z., Dong, C., Lou, W.: Searchable symmetric encryption with forward search privacy. IEEE Transactions on Dependable and Secure Computing 18(1), 460–474 (2019) https://doi.org/10.1109/TDSC.2019.2894411 DOI: https://doi.org/10.1109/TDSC.2019.2894411
[4] Wang, Q., Zhang, X., Qin, J., Ma, J., Huang, X.: A verifiable symmetric searchable encryption scheme based on the avl tree. The Computer Journal 66(1), 174–183 (2023) https://doi.org/10.1093/comjnl/bxab152 DOI: https://doi.org/10.1093/comjnl/bxab152
[5] Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In International Conference on the Theory and Applications of Cryptographic Techniques, pp. 506–522 (2004). https://doi.org/10.1007/978-3-540-24676-3_30 DOI: https://doi.org/10.1007/978-3-540-24676-3_30
[6] Liang, K., Susilo, W.: Searchable attribute-based mechanism with efficient data sharing for secure cloud storage. IEEE Transactions on Information Forensics and Security 10(9), 1981–1992 (2015) https://doi.org/10.1109/TIFS.2015.2442215 DOI: https://doi.org/10.1109/TIFS.2015.2442215
[7] Xia, Z., Wang, X., Sun, X., Wang, Q.: A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE transactions on parallel and distributed systems 27(2), 340–352 (2015) https://doi.org/10.1109/TPDS.2015.2401003 DOI: https://doi.org/10.1109/TPDS.2015.2401003
[8] Byun, J.W., Rhee, H.S., Park, H.-A., Lee, D.H.: Offline keyword guessing attacks on recent keyword search schemes over encrypted data. In Workshop on Secure Data Management, pp. 75–83 (2006). https://doi.org/10.1007/11844662_6 DOI: https://doi.org/10.1007/11844662_6
[9] Hu, C., Liu, P.: A secure searchable public key encryption scheme with a designated tester against keyword guessing attacks and its extension. In International Conference on Computer Science, Environment, Ecoinformatics, and Education, pp. 131–136 (2011). https://doi.org/10.1007/978-3-642-23324-1_23 DOI: https://doi.org/10.1007/978-3-642-23324-1_23
[10] Huang, Q., Li, H.: An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Information Sciences 403–404, 1–14 (2017) https://doi.org/10.1016/j.ins.2017.03.038 DOI: https://doi.org/10.1016/j.ins.2017.03.038
[11] Lu, Y., Li, J., Zhang, Y.: Secure channel free certificatebased searchable encryption withstanding outside and inside keyword guessing attacks. IEEE Transactions on Services Computing 14(6), 2041–2054 (2019) https://doi.org/10.1109/TSC.2019.2910113 DOI: https://doi.org/10.1109/TSC.2019.2910113
[12] Karati, A., Fan, C.-I., Zhuang, E.-S.: Reliable data sharing by certificateless encryption supporting keyword search against vulnerable kgc in industrial internet of things. IEEE Transactions on Industrial Informatics 18(6), 3661–3669 (2021) https://doi.org/10.1109/TII.2021.3112986 DOI: https://doi.org/10.1109/TII.2021.3112986
[13] Shiraly, D., Pakniat, N., Noroozi, M., Eslami, Z.: Pairing-free certificateless authenticated encryption with keyword search. Journal of Systems Architecture 124, 102390 (2022) https://doi.org/10.1016/j.sysarc.2021.102390 DOI: https://doi.org/10.1016/j.sysarc.2021.102390
[14] Liu, X., Sun, Y., Dong, H.: A pairing-free certificateless searchable public key encryption scheme for iomt. Journal of Systems architecture 139, 102885 (2023) https://doi.org/10.1016/j.sysarc.2023.102885 DOI: https://doi.org/10.1016/j.sysarc.2023.102885
[15] Li, J., Wang, M., Lu, Y., Zhang, Y., Wang, H.: Abksskga: Attribute-based keyword search secure against keyword guessing attack. Computer Standards and Interfaces 74, 103471 (2021) https://doi.org/10.1016/j.csi.2020.103471 DOI: https://doi.org/10.1016/j.csi.2020.103471
[16] Lu, Y., Li, J.: Lightweight public key authenticated encryption with keyword search against adaptivelychosen-targets adversaries for mobile devices. IEEE Transactions on Mobile Computing 21(12), 4397–4409 (2021) https://doi.org/10.1109/TMC.2021.3077508 DOI: https://doi.org/10.1109/TMC.2021.3077508
[17] Liu, X., Dong, H., Kumari, N., Kar, J.: A pairingfree certificateless searchable public key encryption scheme for industrial internet of things. IEEE Access 11, 58754–58764 (2023) https://doi.org/10.1109/ACCESS.2023.3285114 DOI: https://doi.org/10.1109/ACCESS.2023.3285114
[18] Cheng, L., Qin, J., Meng, F.: Privacy leakage of certificateless public key authenticated searchable encryption via frequency analysis: Attacks and revises. Computer Standards and Interfaces 87, 103762 (2024) https://doi.org/10.1016/j.csi.2023.103762 DOI: https://doi.org/10.1016/j.csi.2023.103762
[19] Huang, Q., Huang, P., Li, H., Huang, J., Lin, H.: A more efficient public-key authenticated encryption scheme with keyword search. Journal of Systems Architecture 137, 102839 (2023) https://doi.org/10.1016/j.sysarc.2023.102839 DOI: https://doi.org/10.1016/j.sysarc.2023.102839
[20] Qin, B., Cui, H., Zheng, X., Zheng, D.: Improved security model for public-key authenticated encryption with keyword search. In International Conference on Provable Security, pp. 19–38 (2021). https://doi.org/10.1007/978-3-030-90402-9_2 DOI: https://doi.org/10.1007/978-3-030-90402-9_2
[21] Cheng, L., Qin, J., Feng, F., Meng, F.: Securityenhanced public-key authenticated searchable encryption. Information Sciences 647, 119454 (2023) https://doi.org/10.1016/j.ins.2023.119454 DOI: https://doi.org/10.1016/j.ins.2023.119454
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Authors

This work is licensed under a Creative Commons Attribution 4.0 International License.







