A Low-Latency and Secure Data Sharing Method Based on Blockchain and Outsourced Attribute-Based Encryption
DOI:
https://doi.org/10.64509/jicn.12.44Keywords:
Blockchain, low-latency data sharing, outsourced attribute-based encryption, smart contract, edge computing securityAbstract
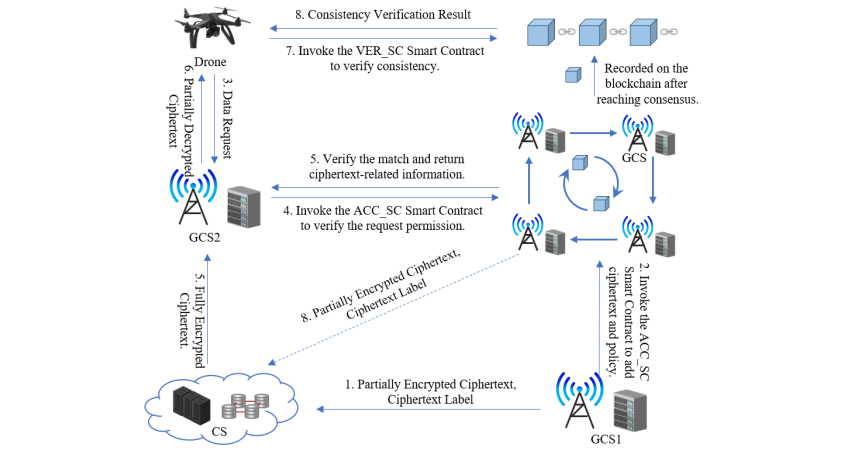
Current data sharing mechanisms face limitations in fine-grained access control, encryption overhead, terminal resource consumption, and result verifiability. These issues make them unsuitable for the low-latency and high-security demands of drone swarm collaboration in cloud-edge-end architectures. To address these challenges, this paper proposes a secure and low-latency data sharing method based on blockchain and outsourced attribute-based encryption. First, in the edge layer, a blockchain network is responsible for enforcing access control, where policy-matching smart contracts enforce fine-grained attribute-based access control. Second, encryption and decryption tasks are outsourced to the edge and cloud, effectively reducing the computational burden on terminal devices. Third, a consistency verification smart contract is introduced to validate outsourced results, ensuring data confidentiality and integrity. Experimental results show that the proposed method significantly lowers system latency and terminal overhead while maintaining strong security, making it suitable for edge-collaborative applications with strict real-time requirements.
Downloads
References
[1] Muchiri, G.N., Kimathi, S.: A review of applications and potential applications of UAV. In Proceedings of the 2016 Sustainable Research and Innovation (SRI) Conference, pp. 280-283 (2022)
[2] Poorvi, J., Kalita, A., Gurusamy, M.: Reliable and efficient data collection in uav based iot networks. IEEE Communications Surveys and Tutorials (2025). https://doi.org/10.1109/COMST.2025.3550274 DOI: https://doi.org/10.1109/COMST.2025.3550274
[3] Kumar, J., Kumar, M., Pandey, D.K., Raj, R.: Encryption and authentication of data using the IPSEC protocol. In Proceedings of the Fourth International Conference on Microelectronics, Computing and Communication Systems, pp. 855-862 (2020). https://doi.org/10.1007/978-981-15-5546-6_71 DOI: https://doi.org/10.1007/978-981-15-5546-6_71
[4] Reimers, E.: On the security of TLS and IPsec: Mitigation through physical constraints. Bachelor Thesis, Linkoping University (2015)
[5] Xia, T., Wang, M., He, J., Lin, S., Shi, Y., Guo, L.: Research on identity authentication scheme for uav communication network. Electronics 12(13), 2917 (2023). https://doi.org/10.3390/electronics12132917 DOI: https://doi.org/10.3390/electronics12132917
[6] Makhdoom, I., Abolhasan, M., Abbas, H., Ni, W.: Blockchain's adoption in IoT: The challenges, and a way forward. Journal of Network and Computer Applications 125, 251-279 (2019). https://doi.org/10.1016/j.jnca.2018.10.019 DOI: https://doi.org/10.1016/j.jnca.2018.10.019
[7] Jiang, Y., Ma, B., Wang, X., Yu, G., Yu, P., Wang, Z., Ni, W., Liu, R.P.: Blockchained federated learning for internet of things: A comprehensive survey. ACM Computing Surveys 56(10), 1-37(2024). https://doi.org/10.1145/3659099 DOI: https://doi.org/10.1145/3659099
[8] Ramos, S., Cruz, T., Simoes, P.: Security and safety of unmanned air vehicles: An overview. In ECCWS 2021 20th European Conference on Cyber Warfare and Security, pp. 357-368 (2021)
[9] Japp, W., Lee, V., Vagicherla, S.A., Rubio-Medrano, C.: Fly-ABAC: Attribute Based Access Control for the Navigation of Unmanned Aerial Vehicles. In 2024 IEEE International Conference on Big Data (BigData), pp. 7471-7476 (2024). https://doi.org/10.1109/BigData62323.2024.10825924 DOI: https://doi.org/10.1109/BigData62323.2024.10825924
[10] Jeong, H.J., Ha, Y.G.: RBAC-Based UAV Control System for Multiple Operator Environments. In the proceedings of the 2012 International Conference on Advanced Software Engineering and Its Applications (ASEA 2012) and the 2012 International Conference on Disaster Recovery and Business Continuity (DRBC 2012), pp. 210-217 (2012). https://doi.org/10.1007/978-3-642-35267-6_27 DOI: https://doi.org/10.1007/978-3-642-35267-6_27
[11] Pang, Y., Chen, Z.: Security Scheme of UAV Flight Control Based on Attribute-Based Access Control Policy. Computer Science 51(4), 366–372 (2024). https://doi.org/10.11896/jsjkx.230200135
[12] Sahai, A., Waters, B.: Fuzzy identity-based encryption. In Annual international conference on the theory and applications of cryptographic techniques, pp. 457-473 (2005). https://doi.org/10.1007/11426639_27 DOI: https://doi.org/10.1007/11426639_27
[13] Liu, Q., Wang, Z., Yu, C., Wang, Z.: Efficient Attribute-Based Encryption Scheme from Lattices for Cloud Security. Netinfo Security, 23(09), 25–36 (2023). https://doi.org/10.3969/j.issn.1671-1122.2023.09.003
[14] Ge, C., Susilo, W., Baek, J., Liu, Z., Xia, J., Fang, L.: A verifiable and fair attribute-based proxy reencryption scheme for data sharing in clouds. IEEE Transactions on Dependable and Secure Computing 19(5), 2907-2919 (2021). https://doi.org/10.1109/TDSC.2021.3076580 DOI: https://doi.org/10.1109/TDSC.2021.3076580
[15] Sun, J., Xu, G., Zhang, T., Yang, X., Alazab, M., Deng, R.H.: Verifiable, fair and privacy-preserving broadcast authorization for flexible data sharing in clouds. IEEE Transactions on Information Forensics and Security 18, 683-698 (2022). https://doi.org/10.1109/TIFS.2022.3226577 DOI: https://doi.org/10.1109/TIFS.2022.3226577
[16] Zhou, Z., Wan, Y., Cui, Q., Yu, K., Mumtaz, S., Yang, C. N., Guizani, M.: Blockchain-based secure and efficient secret image sharing with outsourcing computation in wireless networks. IEEE Transactions on Wireless Communications 23(1), 423-435 (2023). https://doi.org/10.1109/TWC.2023.3278108 DOI: https://doi.org/10.1109/TWC.2023.3278108
[17] Saini, A., Zhu, Q., Singh, N., Xiang, Y., Gao, L., Zhang, Y.: A smart-contract-based access control framework for cloud smart healthcare system. IEEE Internet of Things Journal 8(7), 5914-5925 (2021). https://doi.org/10.1109/JIOT.2020.3032997 DOI: https://doi.org/10.1109/JIOT.2020.3032997
[18] Liu, B., Sun, S., Szalachowski, P.: SMACS: smart contract access control service. In 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), pp. 221-232 (2020). https://doi.org/10.1109/DSN48063.2020.00039 DOI: https://doi.org/10.1109/DSN48063.2020.00039
[19] Feng, C., Yu, K., Bashir, A.K., Al-Otaibi, Y.D., Lu, Y., Chen, S.: Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Network 35(1), 130-137 (2021). https://doi.org/10.1109/MNET.011.2000223 DOI: https://doi.org/10.1109/MNET.011.2000223
[20] Bera, B., Saha, S., Das, A.K., Kumar, N., Lorenz, P., Alazab, M.: Blockchain-envisioned secure data delivery and collection scheme for 5g-based IoT-enabled internet of drones environment. IEEE Transactions on Vehicular Technology 69(8), 9097-9111 (2020). https://doi.org/10.1109/TVT.2020.3000576 DOI: https://doi.org/10.1109/TVT.2020.3000576
[21] Mandal, S., Bera, B., Sutrala, A.K., Das, A.K., Choo, K.R., Park, Y.: Certificateless-signcryption based three-factor user access control scheme for IoT environment. IEEE Internet of Things Journal 7(4), 3184-3197 (2020). https://doi.org/10.1109/JIOT.2020.2966242 DOI: https://doi.org/10.1109/JIOT.2020.2966242
[22] Mandinyenya, G., Malele, V.: Formal Verification of a Blockchain-Based Security Model for Personal Data Sharing Using the Dolev-Yao Model and ProVerif. International Journal of Advanced Computer Science & Applications, 16(9), 444-456 (2025). https://dx.doi.org/10.14569/IJACSA.2025.0160942 DOI: https://doi.org/10.14569/IJACSA.2025.0160942
[23] Zhang, J.: Research on Blockchain-Based Secure Data Sharing Scheme in Cloud-Edge-End Collaboration. Master's Thesis, Beijing Jiaotong University (2024)
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Authors

This work is licensed under a Creative Commons Attribution 4.0 International License.







